
Photo by Dayne Topkin on Unsplash
Email is old tech by Internet standards, and tech companies have been trying to get it to catch up with the modern world for a while now. With all that’s been happening in the email world, it’s hard to make ethical and HIPAA-friendly choices without a little bit of knowledge.
In this article, we here at Person Centered Tech will help you understand the basic lay of the email land so you can choose the email service(s) you need for optimum client service and security.
What Happens When You Send an Email?
Emails live out their virtual lives in three places that we need to think about:
1) Sitting on your computer/smartphone or on the client’s computer/smartphone.
2) Sitting in your email provider’s data center or in your client’s email provider’s data center. (A “data center” is a place where companies house lots of server computers with gigantic Internet connections.)
3) Moving across the Internet between all those things.
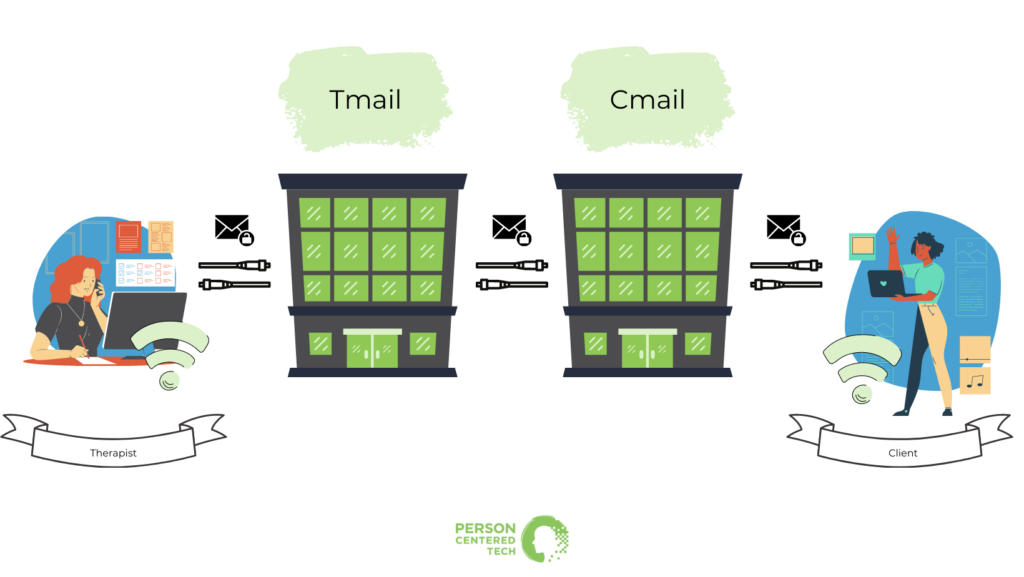
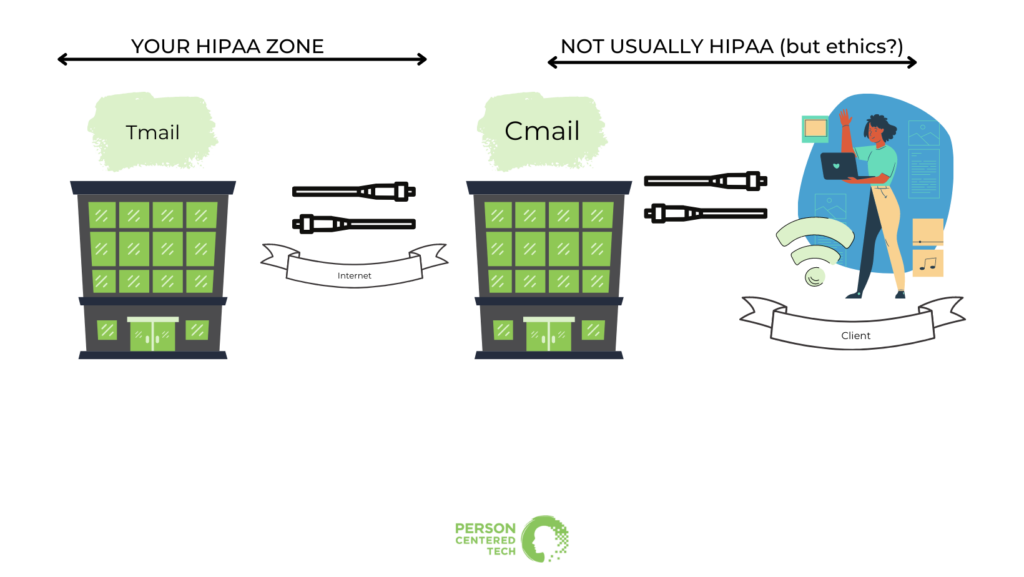
Here we see a therapist and a client exchanging emails via their services at “Tmail” — for TherapistMail — and “Cmail” — for ClientMail. Any resemblance to actual email services living or dead is purely intentional.
In the diagram above, we see the therapist, the client, and their email services’ data centers connected by arrows that represent the Internet.
When an email crosses the Internet to get to its next destination, it passes through many different machines on the way. If that email’s content isn’t obscured by encryption, then it can be read by all of those machines through which it passes.
If the therapist has a HIPAA Business Associate Agreement with Tmail, then she’s fine by HIPAA when she allows Tmail to handle and send the email for her. It’s those pesky Internet connections she still has to worry about.
Fortunately, the Internet connection between the therapist and Tmail is very likely protected by encryption. It’s rare that email services don’t use an encrypted “tunnel,” as it were, for Internet connections when we’re sending emails or downloading emails.
So if the therapist has that all-important BAA with Tmail, then the first leg of the Internet trip is well protected in nearly every case. The same will go for the leg of the Internet trip between Cmail and the client.
It’s that leg in the middle that causes most of the problems:
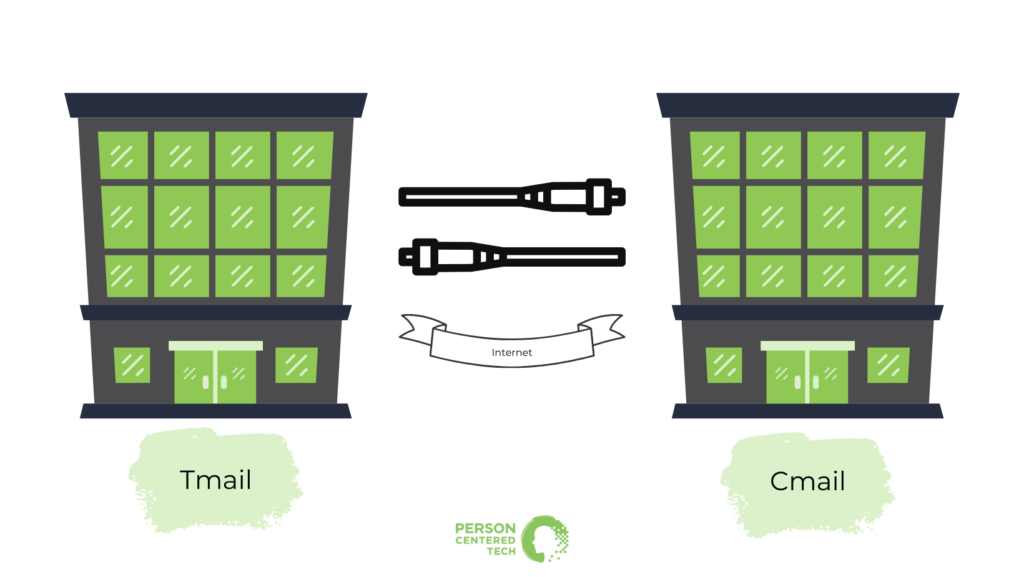
What happens in that leg of the Internet trip? In the words of Ethics professors everywhere, “It depends!” Let’s explore the possibilities in the form of the three kinds of email security as described by Person Centered Tech.
Three Different Kinds of Email Security
Least Reliably Secure: Conventional Email
When sending between the two data centers, email is typically sent “as-is.” The email can be read by anyone with access to the one of the many machines that the email passes through on its way across the Internet. That is how classic conventional email works.
Email was invented very early in the Internet’s life, when the people who were working with it didn’t anticipate a need for security (yes, really). So in this middle leg of the Internet trip, conventional email is sent “in the clear” across the network without anything to hide its contents from prying eyes.
Sometimes, however, modern email companies will make arrangements to use encryption when sending emails to each other. When they do this, they turn a conventional email into a “TLS-Secured Email,” described below. Many companies are working on doing this as often as possible. You can read about it in our article on “safer email.”
Even though conventional email sometimes gets spontaneously upgraded to TLS-Secured email like depicted below, you can’t predict this upgrade and you usually can’t rely on it except in certain specific situations. See our article on “safer email” for some examples of that.
Second-Most Reliably Secure: TLS-Secured Email
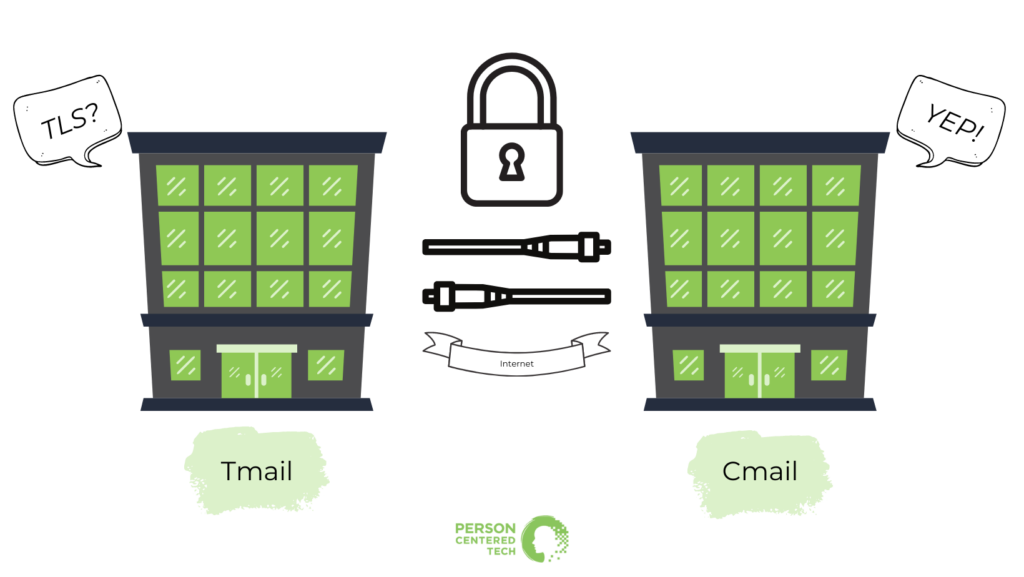 Like described above, we get TLS-secured email when the email providers involved in an exchange agree to use encryption. You usually don’t know when this has happened, except in a few cases. Rob Reinhardt shows us how to find that info on Gmail in his article here.
Like described above, we get TLS-secured email when the email providers involved in an exchange agree to use encryption. You usually don’t know when this has happened, except in a few cases. Rob Reinhardt shows us how to find that info on Gmail in his article here.
TLS-secured email is simple to use, and it helps ensure that emails are encrypted all the way across an Internet transmission. It does not, however, secure emails from any prying eyes that may be present when an email sits in a client’s email provider’s data center or on the client’s computer/smartphone. It only protects transmission across the Internet.
For most clients, there is little to no additional risk posed by that situation. For others, important risks can remain. For more details, see our article on non-Internet risks in using email.
TLS-secured email isn’t feasible 100% of the time because it requires cooperation from the receiving email provider. Without such cooperation, conventional email services will just go ahead and send the email without any encryption!
Most Reliably Secure: Escrow Email
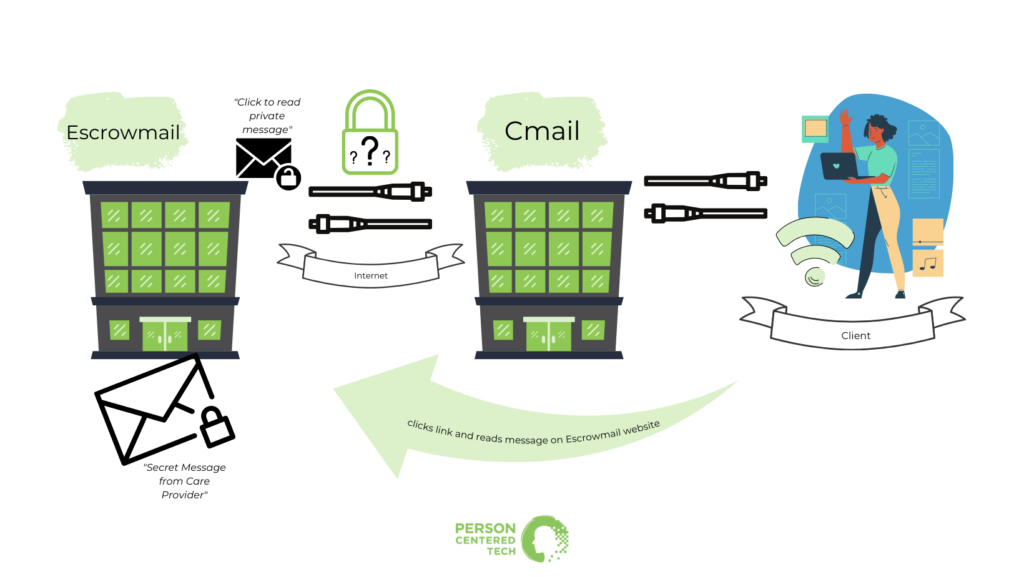
Our therapist has ditched Tmail and is now using Escrowmail in order to make sure that messages are super safe from prying eyes.
Escrow email is so-called because your email service will hold on to your secure message “in escrow,” and invite the intended recipient to come over to their website and read your secure message there.
Escrow email is the kind where you get an email that says, “Your clinician has sent you a secure message. Click here to go read it.” You then click the provided link and it takes you to a webpage on the escrow email provider’s site. Then you do something to authenticate your identity, such as log in to a client portal account, answer a security question, or something like that. After authenticating, you can read the secure message right there on the same webpage. Many hospitals and medical clinics now use escrow email regularly.
Escrow email can be annoying to use, but it provides the best and most reliable and security. Escrow emails never end up in clients’ inboxes or on their phones or computers because they don’t actually get sent over the Internet. Sometimes, for clients, that’s an annoyance. But when you need to ensure that your message or attachment stays away from interlopers in the client’s life, escrow email is one of your best bets.
Even if a snooping employer, school administrator, roommate, or domestic abuser can get into your client’s email account, they likely can’t access the contents of any escrow-secured emails you’ve sent the client. (That is not true of TLS-secured email, which is only secured while it travels over the Internet to the client’s email service.)
Our free, informative articles are brought to you by Hushmail,
who is offering our readers 15% off for life!
Wondering why this is here? See our sponsorship policy for details.

 Roy says: Hushmail is one of several secure email options that serves health care practitioners like us. Hushmail is highly trusted, affordable, includes secure web forms that accept e-signatures, and has earned a recommendation from us for use by mental health professionals. Learn more about Hushmail for Healthcare and get 15% off for life.
Roy says: Hushmail is one of several secure email options that serves health care practitioners like us. Hushmail is highly trusted, affordable, includes secure web forms that accept e-signatures, and has earned a recommendation from us for use by mental health professionals. Learn more about Hushmail for Healthcare and get 15% off for life.
Which Kind of Email Should You Use?
Reasons to Use Conventional Email
There are a couple reasons why conventional email can be attractive to both clinicians and clients:
1) For a particular client, there may be no other choice if they want their therapist to send them emails. It is possible to use conventional email without TLS security and remain HIPAA compliant, although the circumstances are somewhat restricted. See our article on unsecured email and texting for more details.
2) Most (or perhaps all) of the email services that are willing to enter into HIPAA Business Associate Agreements are also willing to engage in TLS security with other email services. Google’s GSuite and Microsoft’s MS 365 are notable examples of such conventional email services.
So if you do it properly and with intentionality, there are several ways that you can use conventional email services — and secure email services that are capable of conventional email, like Hushmail and LuxSci —and maintain HIPAA compliance.
Reasons to Use TLS-Secured Email
There are a few reasons why TLS-secured email can be attractive to both clinicians and clients:
1) Many clients don’t have reason to worry about snooping administrators, bosses, housemates, stalkers, and the like. For them, TLS-secured email covers the email-related security risks that really need to be addressed by the therapist for that client.
For these situations, there are secure email services — most notably Paubox — that default to TLS-secured emails and can fall back on escrow email when a TLS-secured connection is not available.
2) The therapist may only be worried about HIPAA compliance and have little concern for issues beyond that. The scope of your HIPAA requirements around sending an email generally stop once the client’s email service receives the email. Whatever happens after that is likely not covered by HIPAA.
However, it may be worth considering what your ethics codes and colleagues would say regarding professional standards on this point.
The HIPAA Security Rule requires you to secure electronic protected health information that you “create, receive, maintain, or transmit.” After you transmit an email to a client, it usually becomes the client’s own responsibility under HIPAA once their email service receives it.
3) Perhaps the therapist and client agree to only use TLS-secured email the same way they would use conventional email: for low-risk communications about schedule changes and the like. The TLS security means that even these small messages can’t be spied on as they pass over the Internet, and the client would ostensibly know that these messages are safe in their own inbox and on their own computer/smartphone.
Reasons to Use Escrow Email
There are a few reasons why escrow email can be attractive to therapists and to clients:
1) It’s a great way to send very secure documents and messages to people. When clients need records disclosed, letters of summary, superbills, etc., escrow email is great. When clients know that something is really sensitive, they rarely find the inconvenience to be all that bad.
2) Escrow emails can expire. This means that a sensitive document or message can be sent to a client and then, after some period of time, be rendered unavailable to them. This ensures that bad guys who really want to pry and get into those escrow email messages have a limited time to accomplish their nefarious goal.
An email sent directly to the client can’t be taken back, which makes expiring messages impossible with conventional or TLS-secured email. Escrow services can do it. Note that the therapist’s escrow email service can (and usually does) still keep the message in the therapist’s “Sent” folder for permanent access. That way the therapist can access it indefinitely, but no one else can.
Person Centered Tech’s Recommendation
You should get a secure email service!
Pretty much all secure email services designed for health care will do escrow email. Some will do the try-TLS-but-fall-back-on-escrow thing, too. See all of our reviews of secure email services here.
Some therapists have a HIPAA-friendly conventional email service (e.g. GSuite or Microsoft 365) and also a HIPAA-friendly secure email service. Why? GSuite and MS 365 include a ton of other great features which are also covered by their HIPAA Business Associate Agreement. (As an aside: if clients are clamoring to send you convenient messages about scheduling and other small matters, secure texting is cheap and easily available these days. Read here for details.)
Some therapists integrate secure email services into their GSuite or MS 365 account. There are only a few such services available at any given time.
Still other therapists just use a single secure email service for all their email needs, whether it’s conventional, TLS-secured, or escrow.
There’s no one right choice for everyone. Simply examine your practice’s email needs, compare them to the options available, and make the best choice for you and your clients.

Hi Roy! Something that is not entirely clear in this article is what the scene looks like for HIPAA-friendly services like G suite and such. Do they guarantee using TLS, or do they still need cooperation from the recipient e-mail service? And if the latter, what makes them more secure than standard gmail or whatever? But if the former, you seem to say that the encryption stops at Cmail’s data provider – so couldn’t there be nasty people there who are reading those emails anyway?
HI Roy, I am using NeoCertified encrypted email. It is not on you list of secure email providers. Does this mean I should use only one on your list? Thank you.
Hi Timothy,
Our reviews are done on an ongoing basis as our members request that we review certain products and then as our review team gets to those products in the queue. Lack of presence on the list doesn’t have any specific meaning. :)
If you would like to be able to request we review certain products, you need only become a member. Check it out here: Support Service Membership
-Roy
Hi Raffi,
The parts on conventional email cover Gsuite. Check it out again. :)
Gsuite is more appropriate for HIPAA covered entities because they will execute a BAA with you. They also don’t mine your emails for advertising data (and other purposes) like free Gmail does. Remember, if you can’t figure out what commodity a company is selling, the commodity is probably you. :)
Do you need the g suite business account to get the secure email?
Hi Karen,
The answer to that depends on what you mean by “secure.” Don’t forget that as a member you can ask us any and all of your questions and we’ll be glad to address them — and directly discuss them with you — during Office Hours, so please don’t hesitate to make use of that! You can submit your questions here.