
Build Inc BYOD Self-Audit Help & Device Security Instruction Center
This page is here to help you, a member of the Build Inc team, abide by Build Inc’s Bring Your Own Device Policy. Below is an orientation training to introduce the purpose and importance of the BYOD policy and its required measures, how to utilize this help center resource, and complete the device registration form.
Configure Your Devices' Technical Security
Gather all your devices that you utilize to conduct any practice business (i.e. access your practice email account, the practice management system, to communicate with clients etc.,) and that handle or contain any protected health information/client info. For each device, print out a copy of the Build Inc BYOD Registration Form.
Download the BYOD Registration Form Here!(print version)
Download the BYOD Registration Form Here! (fillable version)
Trouble adding your signature to the PDF?
- Watch this video for how to add it if you have a Macintosh computer.
- Click this link to read a short article on how to add it if you have a PC computer.
Click on your device below for a list of action items to do. Typically, each action item will have an instructional video showing how to complete it! Fill out the BYOD registration form as you complete each step.
Behavioral Safety Measures
The behavioral security requirements of the BYOD policy are not listed on the device registration form, but they are very important to keeping client information secure. Following are some helpful instructions and tutorials for how to make small changes to your behavior that will support the security of clients and Build Inc.
1) Never connect to untrusted WiFi
WiFi is everywhere, but it’s a bit shocking just how unsecure most WiFi is.
Very importantly: avoiding untrusted WiFi isn’t just important when you are accessing Build Inc systems or working with client information. Using untrusted WiFi can easily cause your device to get infected or cloned (that’s where a bad guy makes a virtual copy of your phone, essentially.)
Devices that contact client information need to be protected from these harmful situations. So they should never be connected to WiFi that you can’t trust. For that reason, BYOD devices should only be connected to WiFi at Build Inc facilities, and to home WiFi where you have set up a secured branch of your WiFi that is not shared with anyone else, including guests.
In cases where you do not have access to trusted WiFi and you need to access the Internet, the best solution is to use your phone’s data plan. If you need to use a computer, your phone can usually be set up to act as its own private WiFi hotspot. That is a very reliable way to make sure you always have trustworthy WiFi for your BYOD devices.
2) When traveling with a device, always carry it with you
We know it is tempting to leave devices in the car while you run into the store, but that is one of the most common ways that devices get stolen and data breaches occur. Even when we put computing devices in the car’s trunk, historical data shows us that they get stolen frequently enough that a car trunk isn’t quite safe enough for the needs of mental health professionals.
So when traveling with BYOD devices, always carry them with you.
Device Checklist
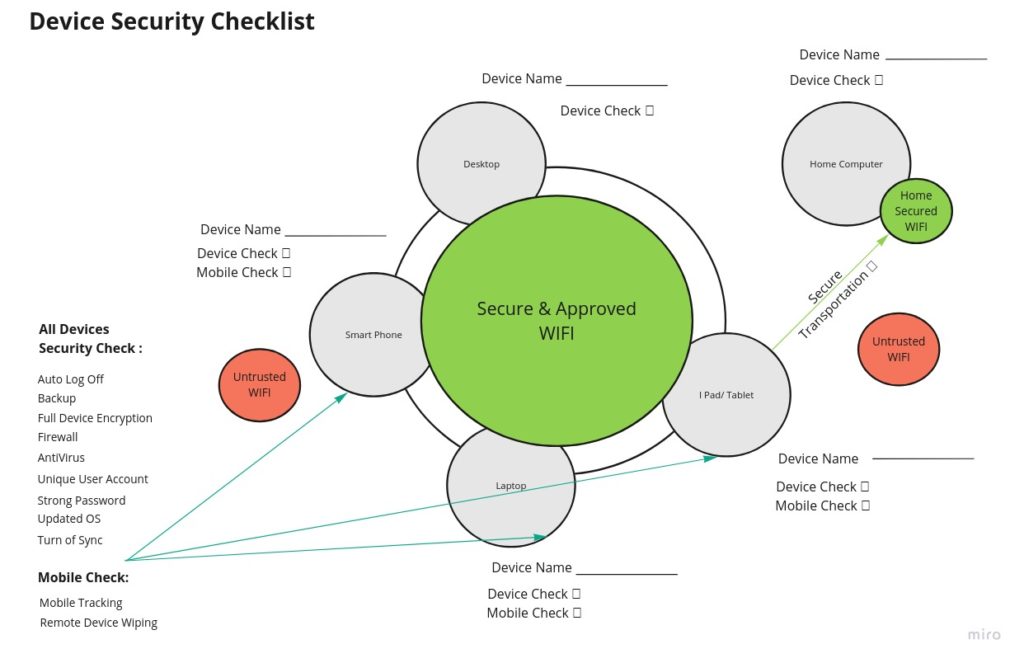
Click the image to get a full-sized version and download.
For a Windows computer: Right-click (click with the right mouse button) on the link and select “Save as.”
For a Mac computer: Hold down the “control” key while clicking on the link and select “Save as.”
